Lies and Spies and All Five Eyes: What’s Going On At CSEC?
While the NSA in the United States and GCHQ have come under a lot of scrutiny and criticism for their actions in terms of mass surveillance of their citizens, the role that CSEC (the Canadian equivalent) has played has been subject to significantly less attention. All three countries are part of an intelligence sharing program called Five Eyes that also includes Australia and New Zealand. If you follow me on Twitter or Facebook or wherever else you may have noticed that I’ve spent a lot of time complaining that Canada’s role in the coalition had not been reported on nearly enough and that our intelligence services were surely involved in some of the misdeeds that the other spy organisations were taking part in.
A few details began trickling out last fall, but nothing like the broad public surveillance that had been revealed in the U.S. or Britain. Back in October it was reported that CSEC had hacked the Brazilian Ministry of Mines and Energy but that was economic espionage, not mass surveillance. In late November the CBC reported that the NSA had “conduct[ed] widespread surveillance in Canada during the 2010 G8 and G20 summits” but the source document didn’t really back that assertion up. The document states that the NSA had assessed that there was no credible information that Islamic extremists were planning to attack the summits (the kind of legitimate work one might want a spy organisation to do) but said nothing that would indicate that there was mass surveillance of private citizens at or around the summits.
But over the past week or so we’ve finally started to learn about CSEC’s role in some of the more nefarious kinds of work that the other Five Eyes countries have been involved in. The Guardian reported that the NSA and GCHQ had a program to collect private info on the users of smartphone games like Angry Birds by taking advantage of the lax security evident in the ad networks that help fund many smartphone games. One thing that went unreported in every story that I saw about this program failed to notice a detail written in one of the slides that The Guardian published.

You’ll notice that the slide says that it was CSEC – Canada’s electronic spying agency – that ported this program to the Android platform. CSEC seems to have played a pretty important role in the plan to collect the private info of users of smartphone apps. As I say, this went almost entirely unreported but it was the first solid piece of evidence that we had that Canada was playing an important role in some of the Five Eyes’ more troublesome activities.
Later last week it was reported in The Huffington Post that the NSA had spied on a large number of people at the 2009 UN climate negotiations in Denmark. The source document that The Huffington Post used for their story claimed that:
analysts here at NSA, as well as our Second Party partners, will continue to provide policymakers with unique, timely, and valuable insights into key countries’ preparations and goals for the conference, as well as the deliberations within countries on climate change policies and negotiation strategies. (emphasis added)
The “Second Party partners” have widely been interpreted to mean the other Five Eyes countries, meaning Canada was likely involved in wide-scale eavesdropping at the climate conference.
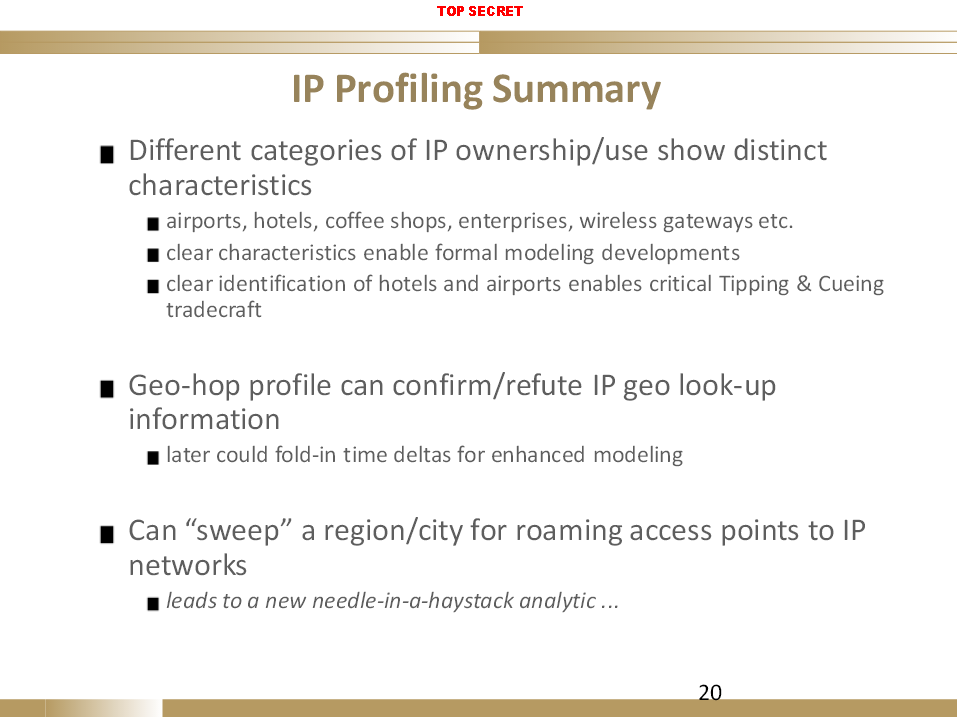
But the most troubling story so far was published by the CBC late last week, when they reported that “CSEC used airport Wi-Fi to track Canadian travellers.” This story considerably undersold what had actually gone on though. If you read the full slideshow that the article was based on it’s pretty apparent that CSEC spied on Canadians in a whole host of places, not just airports. The slideshow suggests that the idea of collecting wi-fi info on travellers from an airport was simply an example and a test case for the broader program that they were developing. Look at the following two slides:
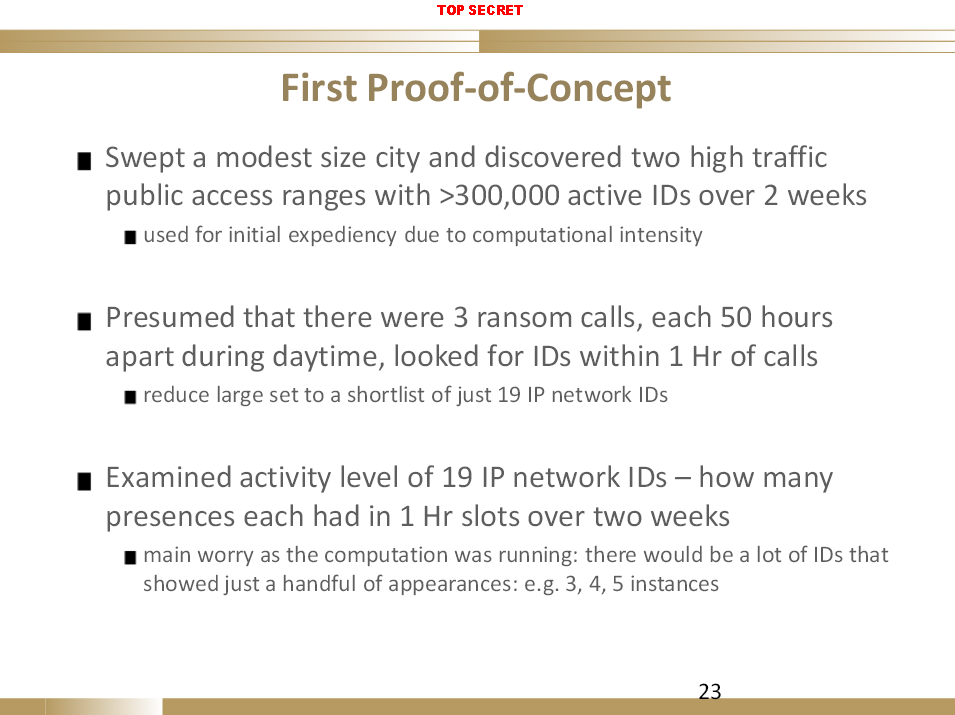
The first slide makes it clear that airport wi-fi was one of a number of kinds of public wi-fi networks they spied on (other slides give more detail on this point). The second slide states, quite clearly, that CSEC carried out a “proof of concept” in which they collected info on hundreds of thousands of wireless Internet connections inside a Canadian city. They did not just spy on Canadians in an airport, they spied on Canadians inside a Canadian city using other wireless access points, and the slideshow on the whole suggests that the plan was to enable this technology to be used in Canada (and elsewhere) in the aid of law enforcement activities; not to track terrorists.
It’s possible that the example given in the slideshow, tracking a kidnapper across Canada, is just an example to demonstrate the idea and that the technology was only ever intended to be used in practice overseas to track terrorists. But nothing in the slideshow suggests this; indeed, the details in the document seem to indicate that this could be deployed domestically. And even if one grants that the general plan may be to track terrorism-related suspects, that does nothing to diminish the fact that the slideshow indicates that on at least two occasions this technique has already been deployed in Canada.
This brings us to a number of comments made recently by the Minister of Defence (Rob Nicholson) and the Deputy Head & Chief of CSEC (John Forster). All subsequent quotes from either man are taken from Aaron Wherry’s piece on this subject at Macleans. One thing that quickly becomes apparent is that Nicholson and Forster are quite happy to use the kinds of obfuscating, avoiding answers that representatives of the NSA have given to the U.S. Congress. They frequently try to re-frame issues or redefine words so that they can give the answers they want.
Nicholson claimed that:
CSEC made it clear to the CBC that nothing in the documents they had obtained showed that Canadian communications were targeted, collected or used, nor that travellers’ movements were tracked.
This is a favourite tactic of the NSA: claim that “communications” and “content” were not collected, rather than answer substantive questions about what was collected. No one claims that CSEC collected individual “communications”. It’s widely acknowledged that what they collected is metadata. Among many others, Ontario’s Information and Privacy Commissioner has explained how metadata can be incredibly revealing, often every bit as revealing as the “content” of “communications”. As for the claim that no travellers’ movements were tracked, that’s flatly contradicted by the slideshow. Slides 8-18 describe the technique they used. This particular slide is the one that most plainly contradicts the Defence Minister’s remark:
Oversight for CSEC’s activities is primarily the responsibility of just one man, the CSEC Commissioner. Nicholson said that:
past commissioners have reviewed CSEC metadata activities and found them to be in compliance with the law and be subject to comprehensive and satisfactory measures to protect the privacy of Canadians.
This is misleading. Here’s what the Commissioner himself said just last summer:
I had no concern with respect to the majority of the CSEC activities reviewed. However, a small number of records suggested the possibility that some activities may have been directed at Canadians, contrary to law. A number of CSEC records relating to these activities were unclear or incomplete. After in-depth and lengthy review, I was unable to reach a definitive conclusion about compliance or non-compliance with the law.
That’s not a ringing endorsement. In fact, that’s the Comissioner saying quite clearly that CSEC did not provide him with the information necessary to reach a proper conclusion, but he expresses concern that Canadians were spied upon illegally.
CSEC is not the only Canadian spy agency to have problems obeying the law. Last December a federal judge found that CSIS (Canada’s equivalent to the CIA)
purposely misled him when he granted it numerous warrants beginning in 2009 to intercept the electronic communications of unidentified Canadians abroad suspected as domestic security threats.
“This was a breach of the duty of candour owed by the service and their legal advisers to the court,” Mosley said in his Further Reasons for Order.
Indeed, Judge Mosley also said that “The failure to disclose that information was the result of a deliberate decision to keep the court in the dark about the scope and extent” of CSIS and CSEC’s activities and that CSIS/CSEC’s actions have “led to misstatements in the public record about the scope of the authority granted the service.” Misstatements like the one Nicholson made when he claimed that CSEC had been found to be in compliance with the law, it would seem.
The head of CSEC provided the same kind of evasive answers as the Defence Minister: “The work relied on metadata … metadata is data about a communication. It’s not the content of a communication.” But no one has claimed that CSEC collected the “content of a communication” so this is entirely irrelevant.
According to CSEC Chief Forster, “This was not an operational surveillance program.” This is contradicted by the CBC article on the program which states that “Sources tell CBC News the technologies tested on Canadians in 2012 have since become fully operational.” Indeed, it’s even contradicted by Forster’s own remarks as he “claimed to be aware of two cases in the past 12 months in which these models had been used to find ‘legitimate foreign targets’.”
So we are left with this: through CSEC (and possibly to a lesser extent CSIS) Canada is an active partner in NSA and GCHQ efforts to spy on a wide variety of people. Experts including academics, a federal court judge, and the CSEC Commissioner have all stated either that Canada’s spy organisations have broken the law or that they seem likely to have done so. The answers provided by the Defence Minister and the Chief of CSEC are evasive and obfuscatory and they are at odds with publically available evidence. This is not democratic and it is not sufficient. Canadians deserve answers and they should demand them.